A Biased View of It Services Melbourne
All about Managed It Services For Law Firms
Table of ContentsSome Known Questions About Managed It Services.The Greatest Guide To Managed It ServicesIt Service Melbourne for BeginnersSome Ideas on It Service Melbourne You Need To Know
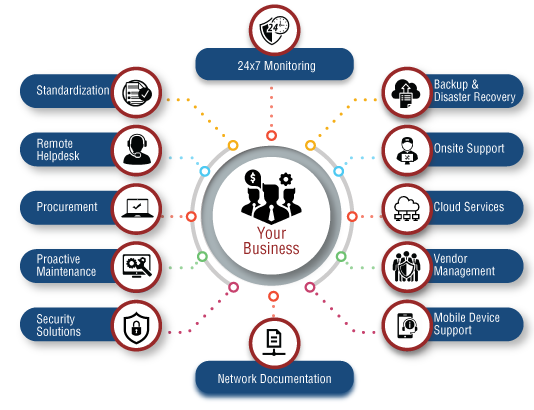
As foresaid, IT sustain offers end-to-end managed IT solutions, that include these primarily: An IT facilities has a number of laptop computers, workstations, printers, web servers as well as hardware systems. A tiny damage or failure may finish up in a fantastic loss, which might be of important data or info. This happening inevitably effect on the firm's returns as well as connection.These policies have multi-factor verification, stopping out of the state logins as well as many other ones in a fantastic role. This is exceptionally for the firms that permit staff members to utilize their very own phones for executing jobs. This bring-your-own-device (BYOD) is not every usual, however still exists. The assistance giving business position their group to safeguard that data as well as properties from cyberpunks or abuse.
It makes certain that only protected devices will certainly be able to carry out from another location, as they would certainly be qualified of safeguarding the delicate information of the business. It refers to the on-demand schedule of computer system sources, consisting of data storage and also computer power. This taking place does not call for any straight active administration by the customer.
As its benefits are fantastic, an increasing number of firms have actually started shifting to the cloud for hosting their information. managed it services. For keeping their confidential info concerning clients as well as their client experience (CX) safe, it features some extraordinary safety and security features. The tech assistance group manages it well in two ways: Making certain configuring as well as taking care of the cloud system for organizing a variety of requisite applications, information monitoring, IT support and also downtime, Providing the full safety and security to what comes under the handled IT solutions from cyber lawbreakers.
The Buzz on It Services Melbourne

Something failed. Wait a moment as well as try again Try again.
Companies are progressively moving their IT infrastructures into the cloud (it services melbourne). Many business organizations now operate in multi-cloud environments or utilize hybrid on-premises and cloud-based IT styles. These complexities necessitate the demand for IT support services to deal with these systems. Cloud computing assistance is an IT service that assists organizations handle their cloud-based framework.
It Services Melbourne for Beginners
Involves screening information recuperation options to make certain that they are trustworthy as well as effective in the event of a data loss or corruption. IT support is essential for businesses that depend greatly on their information, such as those in the health care and also money markets.
Office modern technology alters rapidly and also gets much more intricate by the year. Whereas the mass of work-related computer once occurred within the workplace walls as well as inside a secure border, today's distributed workforce carries out service from homes, coffee bar, cars actually anywhere with web gain access to. Supporting as well find as safeguarding the myriad gadgets as well as accessibility points workers now count on to remain productive has actually developed a whole lot even more benefit IT teams that typically are currently spread also thin.
Organizations rely on managed services service providers (MSPs) for a selection of reasons, yet the majority of frequently, they are used by companies with no interior IT group or those that desire to utilize their internal IT experts to concentrate on certain efforts rather than operational responsibilities for handling innovation. MSPs give a substantial variety of services from the basics such as assistance workdesk support as well as maintaining IT equipment as well as services working completely up to supplying the full collection of IT capabilities, including cyber safety, internet connection, application assistance, data backups, and also calamity recuperation.
Managed It Services Melbourne Can Be Fun For Everyone
Handled IT services are much from one-size-fits-all, so partnering with an MSP who recognizes your organization and is actively purchased aiding you satisfy your goals is vital.
Prospective dangers outside the network are protected against, guaranteeing that Homepage a company's delicate data remains inside. Organizations can go even more by specifying added inner boundaries within their network, which can supply improved protection and access control. Access control defines individuals or groups and the devices that have accessibility to network applications and systems consequently denying unauthorized accessibility, as well as perhaps dangers.
A susceptability is a weakness for circumstances in a software application system and also a make use of is an attack that leverages that vulnerability to obtain control of that system. Sandboxing observes the documents or code as they are opened and looks for malicious habits to protect against hazards from getting on the network. Malware in data such as PDF, Microsoft Word, Excel and also Power, Factor can be safely spotted and obstructed prior to the data get to an innocent end individual.